Connect with Customers.
Disconnect from Risks.
CrowdStrike

Automated Threat Intel Enforcement: Take Predictive Security to the Next Level
The threat landscape changes fast, but ThreatSTOP and CrowdStrike’s joint solution moves even faster thanks to security automation. New and emerging IoCs discovered by CrowdStrike can be added to firewall and DNS rules at machine speeds, outpacing threat actor efforts to avoid detection and mitigation. Complete your continuous 360-degree breach prevention with a proactive network-layer of threat defense, perfect for securing IoT and agent-less clients.
CrowdStrike: Seamlessly integrates threat intelligence into endpoint protection.
ThreatSTOP: Seamlessly integrates threat intelligence into network protection.
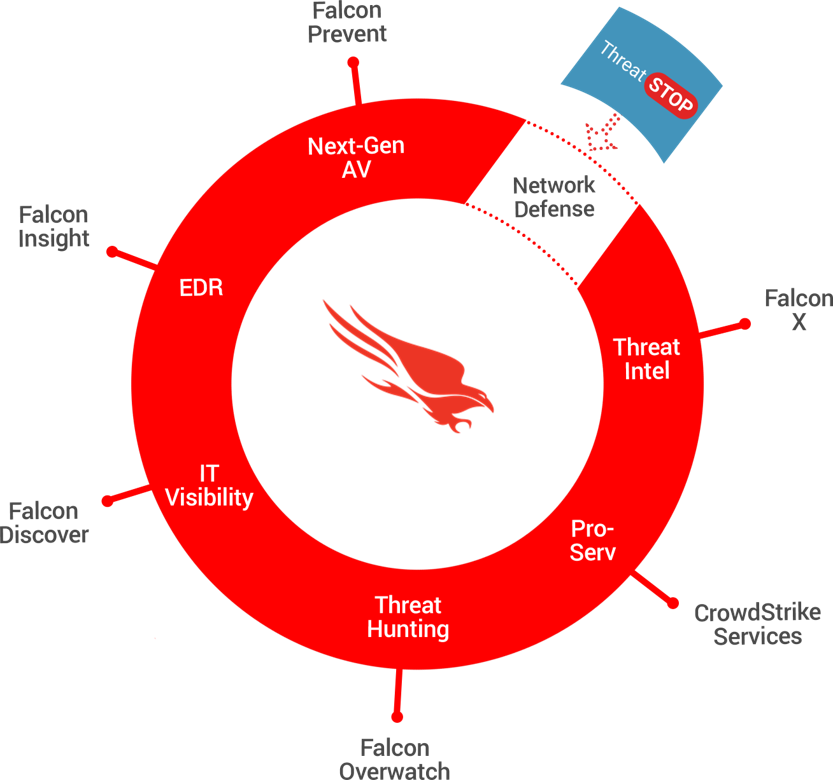
Close the Gap, Protect Everything
- Network-layer protection for clients that aren’t compatible with the Falcon Host, such as IoT devices, servers and databases
- Leverages CrowdStrike’s comprehensive and actionable threat intelligence to proactively block malicious IP connections and DNS requests
- Automated SaaS security service is broadly compatible with leading NGFW, Router, Switch, IDS/IPS, DDI/IPAM, and DNS Servers

PROACTIVE SECURITY. Threats should be blocked, not just alerted on. Drop threats at the network edge.
DEPLOY OVER LUNCH. Deployment takes about an hour with no heavy lifting, and security results are immediate.
ENGAGE AUTOPILOT. Save time and money while super-charging security with an automated, cloud powered solution


Operationalize CrowdStrike Threat Intelligence to Extend Breach Protection to Every Device in Your Network
- CrowdStrike Threat Intelligence: Falcon Intelligence delivers comprehensive, actionable IoCs, and Falcon X delivers tailored IoCs automatically to ThreatSTOP.
- The ThreatSTOP Platform receives continuous IoC updates from the Falcon Platform, transforming them into dynamic policies.
- Network Appliances: ThreatSTOP delivers continuously updated policies containing Falcon Intelligence IoCs directly to your firewalls, routers, DNS servers and more.
Solve security challenges
Operationalize Threat Intelligence
Challenge:
Anticipating and preventing attacks before they happen by proactively blocking communication with high confidence IoCs yields significant security results, but accomplishing it requires large multi-vendor purchases and skilled dedicated staff to manage it.
Solution:
Leverage the power of automation that accomplishes real-time operationalized threat intelligence in a fully cloud delivered integration between CrowdStrike Intelligence and your existing firewalls, routers, DNS servers, and more.
Customer Benefit:
By automating real-time updates to network traffic policies using actionable IoCs from CrowdStrike, your network won't communicate with threat actors and the infrastructure used to carry out attacks, without the manual workflows.
Extend Protection to Every Endpoint Device
Challenge:
Company networks are full of connected devices ranging from printers to MRI machines that aren’t compatible with endpoint security solutions, and are frequent vectors for attack. Securing these devices can be expensive and challenging.
Solution:
Utilize the ThreatSTOP and CrowdStrike joint platform solution to automatically apply actionable threat intelligence IoCs as network-layer security where malicious inbound and outbound connections to agent-less devices can be proactively blocked.
Customer Benefit:
Extend the protection enjoyed by endpoints using the Falcon Host to every connected device in the network, including vulnerable IoT devices that are frequently targeted by threat actors due to the challenges of securing them.