Connect with Customers.
Disconnect from Risks.
FirstSTOP
Tools for Incident Responders
Every successful cyber attack can be catastrophic to your customers. Every minute spent to contain the threat and isolate the enterprise from attackers counts. The comprehensive ThreatSTOP threat intelligence platform can be deployed in monitor-only mode in minutes, with fast compromised asset identification and a seamless transition to containment and recovery.
FirstSTOP Gives Incident Response Analysts Access To:
-
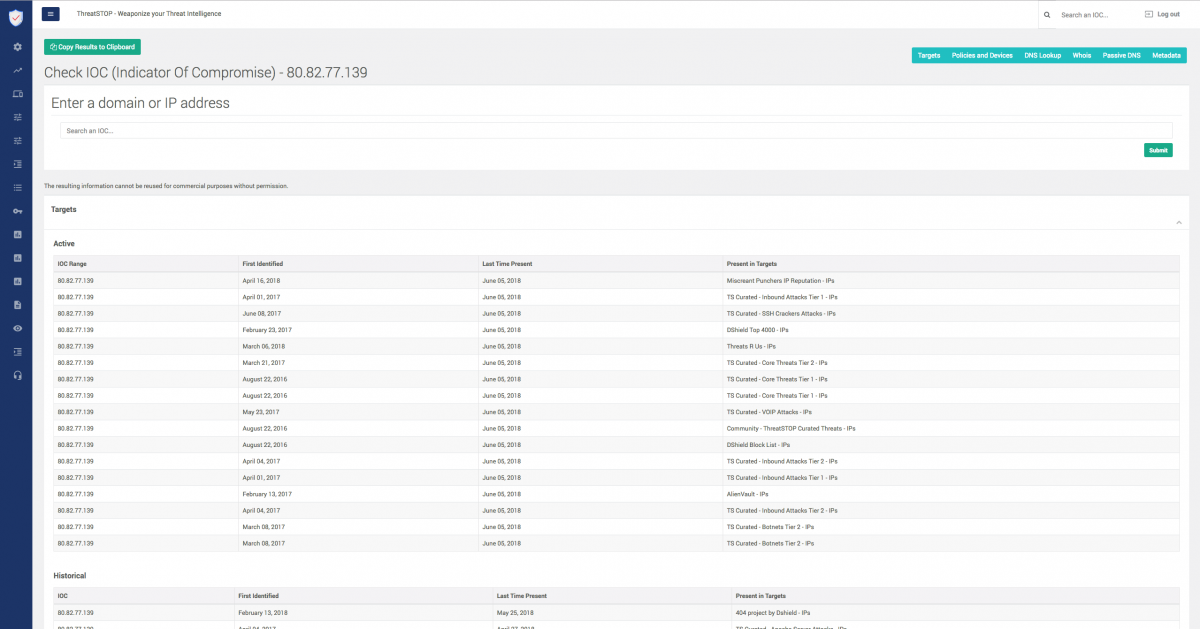
Check IoC Subscription
- Preconfigured, downloadable ISO versions of ThreatSTOP's IP and DNS Defense solutions for hunt and asset identification.
- 20 free licenses for ThreatSTOP's MyDNS Roaming Defense
- Defense agents to correlate network and endpoint incidents.
- Option to add a 30 day limited customer deployment in "block" mode, at no charge.
- Policy customization for targeted hunting.
- Logs and reporting for immediate insight.
Features & Benefits
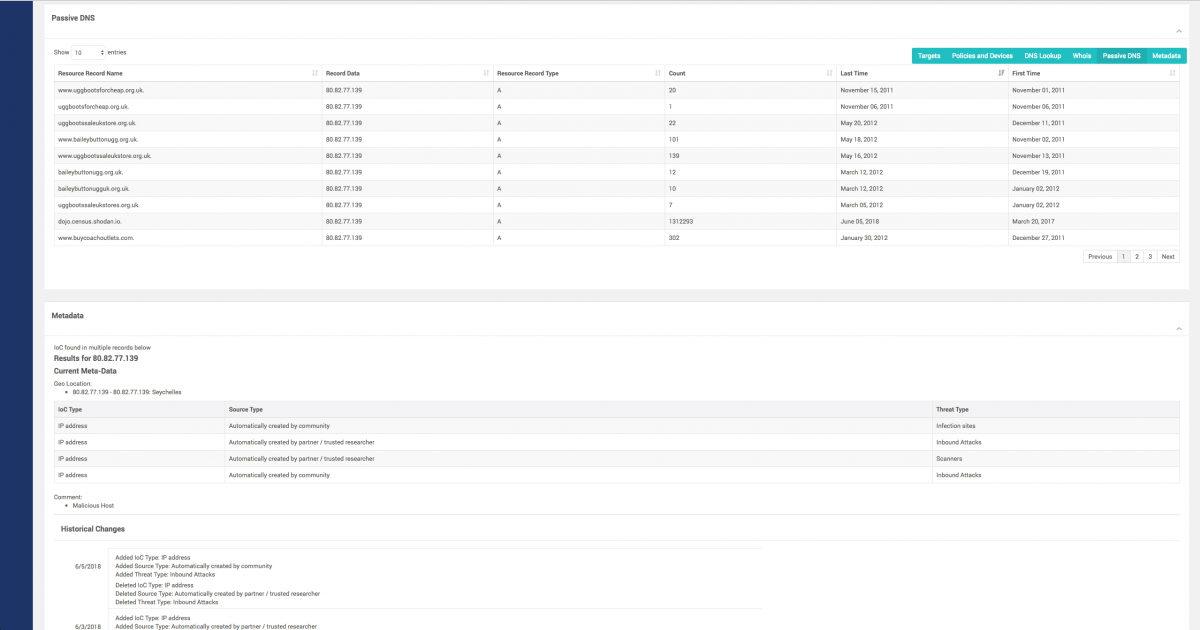
- Rich Metadata & Passive DNS.
- Our database of known malicious IPs has grown: 24 million indicators of compromise to keep you safe.
- Easy to use: Optional API Service available to automatically check for indicators of compromise.
No New Hardware or Software
- 100% Cloud-based Security as a service
- Deploys in under an hour via an online portal
- Custom, user-defined policies are easy to create and manage
- Compatible with all major DNS servers including Windows Server 2016 and Microsoft Azure
Check IoC
Passive DNS & metadata
Start a 30-day trial
To get started with FirstSTOP including a CheckIOC Subscription, try us out for free (no credit card required) for 30 days. You'll be set up in minutes. Or buy now.
ThreatSTOP has eliminated manual blacklisting and remediation, and reduced help desk tickets related to malware by 90%, to only 1-2 per month.
Mike Connors, Information Security Analyst
Threats blocked today
Updated every 15 minutes
Free Trial
See what your other security products have been missing. Start Stopping Threats today at the DNS layer. Quick, easy setup.
