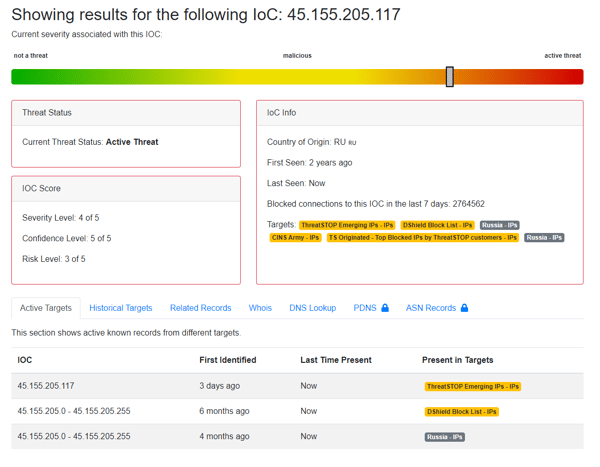
July 6, 2021 • Ofir Ashman
More Love from Russia - More Bad IPs by Selectel like 45.146.164[.]38
1Min read
•
threat intelligence,
IOCs,
malicious IP,
new domains,
dga,
threatstop-blocklists,
selectel
![More Love from Russia - More Bad IPs by Selectel like 45.146.164[.]38](https://www.threatstop.com/hs-fs/hubfs/ip_selectel.png?width=600&height=400&name=ip_selectel.png)
![When Good IPs Behave Badly - like 146.88.240[.]4](https://www.threatstop.com/hs-fs/hubfs/orisitv2.png?width=600&name=orisitv2.png)
![45.146.165[.]168 exploiting Log4j is another reason to block Selectel](https://www.threatstop.com/hs-fs/hubfs/selectel_ip_virustotal.png?width=600&name=selectel_ip_virustotal.png)